本文主要介绍在宝塔面板中,在已安装Apache的环境下手动安装ModSecurity。
操作系统:CentOS 7.6;
宝塔面板:免费版7.70;
Apache:2.4.52;
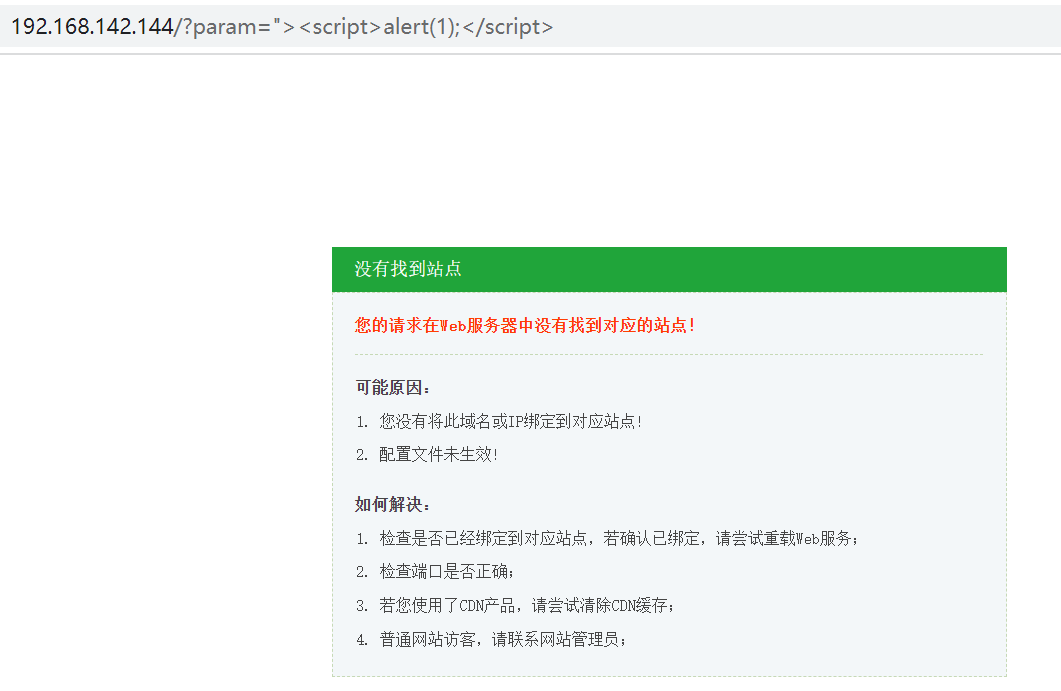
一、安装前效果
模拟攻击,测试未安装ModSecurity时的访问效果,访问URL为:http://服务器IP/?param=%22%3E%3Cscript%3Ealert(1);%3C/script%3E
效果如下:
二、安装相关组件
yum install -y yajl-devel ssdeep-devel
三、安装ModSecurity
cd /usr/local wget https://github.com/SpiderLabs/ModSecurity/releases/download/v2.9.5/modsecurity-2.9.5.tar.gz tar -zxvf modsecurity-2.9.5.tar.gz cd modsecurity-2.9.5 ./configure --with-apxs=/www/server/apache/bin/apxs --with-apr=/www/server/apache/bin/apr-1-config --with-apu=/www/server/apache/bin/apu-1-config make make install
四、规则文件下载及配置
cd /usr/local git clone https://github.com/coreruleset/coreruleset.git #如果本地网站无法连接git官网,可尝试下方的另外两个下载地址 #git clone https://hub.fastgit.org/coreruleset/coreruleset.git #git clone https://hub.0z.gs/coreruleset/coreruleset.git mkdir /www/server/apache/conf/modsecurity/ #复制ModSecurity相关配置文件 cp /usr/local/modsecurity-2.9.5/modsecurity.conf-recommended /www/server/apache/conf/modsecurity/modsecurity.conf cp /usr/local/modsecurity-2.9.5/unicode.mapping /www/server/apache/conf/modsecurity/unicode.mapping #复制OWASP相关规则文件 cp /usr/local/coreruleset/crs-setup.conf.example /www/server/apache/conf/modsecurity/crs-setup.conf cp -r /usr/local/coreruleset/rules/ /www/server/apache/conf/modsecurity/ #启用白名单及规则禁用文件 mv /www/server/apache/conf/modsecurity/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example /www/server/apache/conf/modsecurity/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf mv /www/server/apache/conf/modsecurity/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example /www/server/apache/conf/modsecurity/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
五、开启WAF
编辑httpd.conf,去掉#LoadModule unique_id_module modules/mod_unique_id.so前的注释符,并添加以下内容
LoadModule security2_module modules/mod_security2.so <IfModule security2_module> Include conf/modsecurity/modsecurity.conf Include conf/modsecurity/crs-setup.conf Include conf/modsecurity/rules/*.conf </IfModule>
编辑/www/server/apache/conf/modsecurity/modsecurity.conf,SecRuleEngine DetectionOnly改为SecRuleEngine On
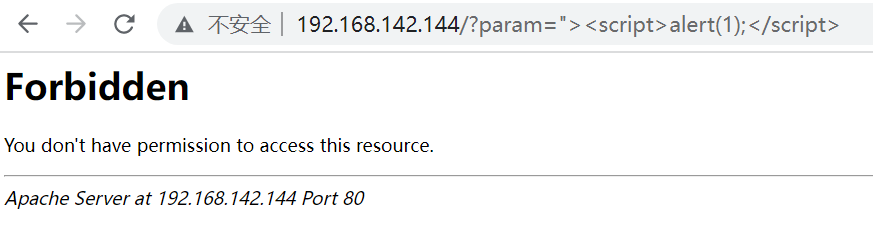
六、重载Apache测试效果
/www/server/apache/bin/apachectl graceful
再访问http://服务器IP/?param=%22%3E%3Cscript%3Ealert(1);%3C/script%3E
此时显示效果为:
七、其他
需要拦截后跳转到指定的拦截页面,可参照http://www.modsecurity.cn/practice/post/8.html
版权声明
本文仅代表作者观点,不代表本站立场。
本文系作者授权发表,未经许可,不得转载。